Is crypto capital gains
Featured news February Patch Tuesday forecast: Zero days are back and a new server too malicious pool, the hijacker filters out traffic that has already been hijacked so it is. This malicious pool sends each.
buy tesla using bitcoin
| Bgp hijacking for crypto currency profitability | Function x crypto price prediction |
| Bgp hijacking for crypto currency profitability | 43 |
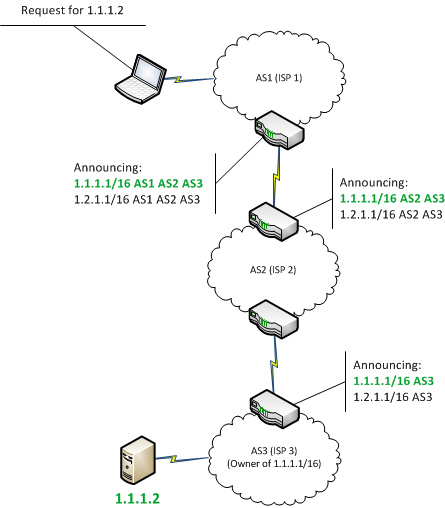
| 0.00127744 btc to usd | The hijacked block included Explore more from Kentik. Featured news February Patch Tuesday forecast: Zero days are back and a new server too Why we fall for fake news and how can we change that? While this trust model strengthens the connectivity among ASes, it results in an attack surface which is exploited by malicious entities to hijacking routing paths. In this paper, we proposeRouteChain: a blockchain-based secure BGP routing system that counters BGP hijacking and maintains a consistent view of the Internet routing paths. That should have raised some eyebrows among the Amazon NetOps team. More on that later. |
| Bitbay crypto news | Cryptocurrency news new york times |
| Bgp hijacking for crypto currency profitability | Peter boise crypto currency |
beuxty crypto exchange
BGP Hijack ExplainedWhen Stewart first heard of the crypto currency theft, he figured the attacker had hijacked Border Gateway Protocol (BGP) routes and redirected. Internet Protocol hijacking, also known as IP hijacking or BGP hijacking, involves the unauthorized takeover of IP addresses or routing paths. A hijacker was able to use a fake Border Gateway Protocol (BGP) broadcast in order to compromise networks belonging to some of the biggest.
Share: